|
 |
|
Categories |
|
|
|
|
|
|
 |
|
Hack tools |
|
|
|
|
|
|
|
|
|
|
|
Useful Stuff
Need a program? A website? A tool? Have one for someone else?
Look here!
.Sol Editor
A flash hacking alternative to variable editing and cheat engine, you can change
values saved bythe game in a “.sol” file. You will find the .SOL files in x:Documents and Settings[account-name]Application DataMacromediaFlash Player#SharedObjects followed by the name of the website. If the game was running from your computer, the .SOL will be in the “localhost” folder. Replace ‘x’ with your main drive, the one with your OS, and the account-name with the currently logged in user. |
Add N Edit Cookies
Firefox Add-on, Cookie Editor that allows you add and edit cookies. |
Aircrack-ng
aircrack is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, thus making the attack much faster compared to other WEP cracking tools. In fact, aircrack is a set of tools for auditing wireless networks. |
Airsnort
AirSnort is a wireless LAN (WLAN) tool which cracks encryption keys on 802.11b WEP networks. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered. |
Autohotkey
AutoHotkey is a free, open-source utility for Windows. * Automate almost anything by sending keystrokes and mouse clicks. * Create hotkeys for keyboard, joystick, and mouse. Virtually any key, button, or combination can become a hotkey. * Expand abbreviations as you type them. For example, typing "btw" can automatically produce "by the way". * Create custom data-entry forms, user interfaces, and menu bars. * Remap keys and buttons on your keyboard, joystick, and mouse. * Convert any script into an EXE file that can be run on computers that don't have AutoHotkey installed. |

Autoit

A VERY useful automation program. I've used it for all of the scripts I have ever made and I would like to see it put on the list. The program even has a very helpful forum to learn how to use the program effectively. |
BFG / hydra
BFG is a modified hydra tool, which now supports generating passwords in brute-force mode, unlike the original hydra. Of course, full source code is provided, and it should compile on all systems where hydra itself compiles, which means all UNIX-
based systems including Linux, BSD, Mac OS, Windows (cygwin), etc. |
 BlueJ BlueJ
BlueJ is an integrated Java environment specifically designed for introductory
teaching. |
Burp

A very powerful website test including spider and possibility to test some exploit
 |
Cain And Abel
Cain & Abel is a password recovery tool for Microsoft Operating Systems.
It allows easy recovery of various kind of passwords by sniffing
the network, cracking encrypted passwords using Dictionary, Brute-Force
and Cryptanalysis attacks, recording VoIP conversations, decoding
scrambled passwords, recovering wireless network keys, revealing
password boxes, uncovering cached passwords and analyzing routing
protocols. The program does not exploit any software vulnerabilities or
bugs that could not be fixed with little effort. It covers some security
aspects/weakness present in protocol's standards, authentication methods
and caching mechanisms; its main purpose is the simplified recovery of
passwords and credentials from various sources, however it also ships
some "non standard" utilities for Microsoft Windows users. Cain & Abel
has been developed in the hope that it will be useful for network
administrators, teachers, security consultants/professionals, forensic staff,
security software vendors, professional penetration tester and everyone
else that plans to use it for ethical reasons. The author will not help o
r support any illegal activity done with this program. Be warned that there
is the possibility that you will cause damages and/or loss of data using this
software and that in no events shall the author be liable for such damages
or loss of data.Please carefully read the License Agreement included
in the program before using it. |
Cheat Engine 5.4

The coolest tool to hack all sorts of games, with powerful commands and friendly interface. Every game hacker must have this tool... * very useful also in browser games |
Chickenfoot
Chickenfoot is a Firefox extension that puts a programming environment in the browser's sidebar so you can write scripts to manipulate web pages and automate web browsing. |
Colasoft Packet Builder
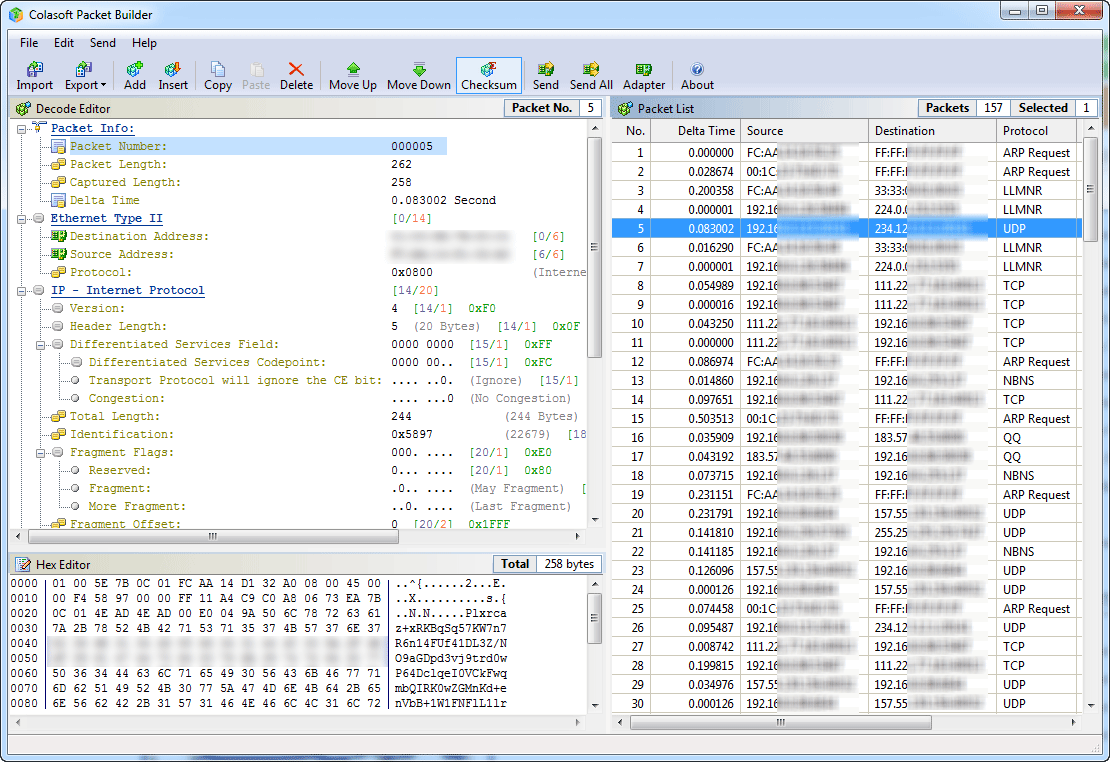 Colasoft Packet Builder enables creating custom network packets; users can use this tool to check their network protection against attacks and intruders. Colasoft Packet Builder includes a very powerful editing feature. Besides common HEX editing raw data, it features a Decoding Editor allowing users to edit specific protocol field values much easier. Users are also able to edit decoding information in two editors - Decode Editor and Hex Editor. Users can select one from the provided templates Ethernet Packet, ARP Packet, IP Packet, TCP Packet and UDP Packet, and change the parameters in the decoder editor, hexadecimal editor or ASCII editor to create a packet. Any changes will be immediately displayed in the other two windows. In addition to building packets, Colasoft Packet Builder also supports saving packets to packet files and sending packets to network. Colasoft Packet Builder enables creating custom network packets; users can use this tool to check their network protection against attacks and intruders. Colasoft Packet Builder includes a very powerful editing feature. Besides common HEX editing raw data, it features a Decoding Editor allowing users to edit specific protocol field values much easier. Users are also able to edit decoding information in two editors - Decode Editor and Hex Editor. Users can select one from the provided templates Ethernet Packet, ARP Packet, IP Packet, TCP Packet and UDP Packet, and change the parameters in the decoder editor, hexadecimal editor or ASCII editor to create a packet. Any changes will be immediately displayed in the other two windows. In addition to building packets, Colasoft Packet Builder also supports saving packets to packet files and sending packets to network. |
Cryptool
 A cryptography Analysis, how-to and cracking program... A cryptography Analysis, how-to and cracking program... |
Dev C++
Bloodshed Dev-C++ is a full-featured Integrated Development Environment (IDE) for the C/C++ programming language. It uses Mingw port of GCC (GNU Compiler Collection) as it's compiler. Dev-C++ can also be used in combination with Cygwin or any other GCC based compiler. |
DollarDNS Crawler
This tool allows one to recursively retrieve the result of any type of DNS record for all name servers a domain specifies |
DollarDNS Whois
DollarDNS Whois Direct allows users to make advanced WHOIS queries against a domain, including raw queries |
DownloadHelper
 "Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded! "Using DownloadHelper, you can easily save videos from most of the popular video sites" -Main Site Lets you download videos from youtube, or almost any other video/music site in a flv format (that you can then convert after download) As simple as click and its downloaded! |
FireGPG
FireGPG is a Firefox extension under MPL which brings an interface to encrypt, decrypt, sign or verify the signature of text in any web page using GnuPG. |
Firebug
 Firebug integrates with Firefox to put a wealth of web development tools at your fingertips while you browse. You can edit, debug, and monitor CSS, HTML, JavaScript, and network activity live in any web page. Firebug integrates with Firefox to put a wealth of web development tools at your fingertips while you browse. You can edit, debug, and monitor CSS, HTML, JavaScript, and network activity live in any web page. |
Firefox
 The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons. The most safe web browser for mac and windows. It has many types of add-ons, including hacking add-ons. |
Firekeeper
Firekeeper is an Intrusion Detection and Prevention System for Firefox. It is able to detect, block and warn the user about malicious sites. Firekeeper uses flexible rules similar to Snort ones to describe browser based attack attempts. Rules can also be used to effectively filter different kinds of unwanted content. |
Flash Hacker (Tamper Data)
 Tamper data is a add on for firefox that is used for hacking flash games(High scores)> If you have trouble using ti or don't know how to use it contact me at ryanb58@100wpd.com Tamper data is a add on for firefox that is used for hacking flash games(High scores)> If you have trouble using ti or don't know how to use it contact me at ryanb58@100wpd.com |
GCC - C compiler
 The GNU Compiler Collection includes front ends for C, C++, Objective-C, Fortran, Java, and Ada, as well as libraries for these languages (libstdc++, libgcj,...). The GNU Compiler Collection includes front ends for C, C++, Objective-C, Fortran, Java, and Ada, as well as libraries for these languages (libstdc++, libgcj,...). |
Geany
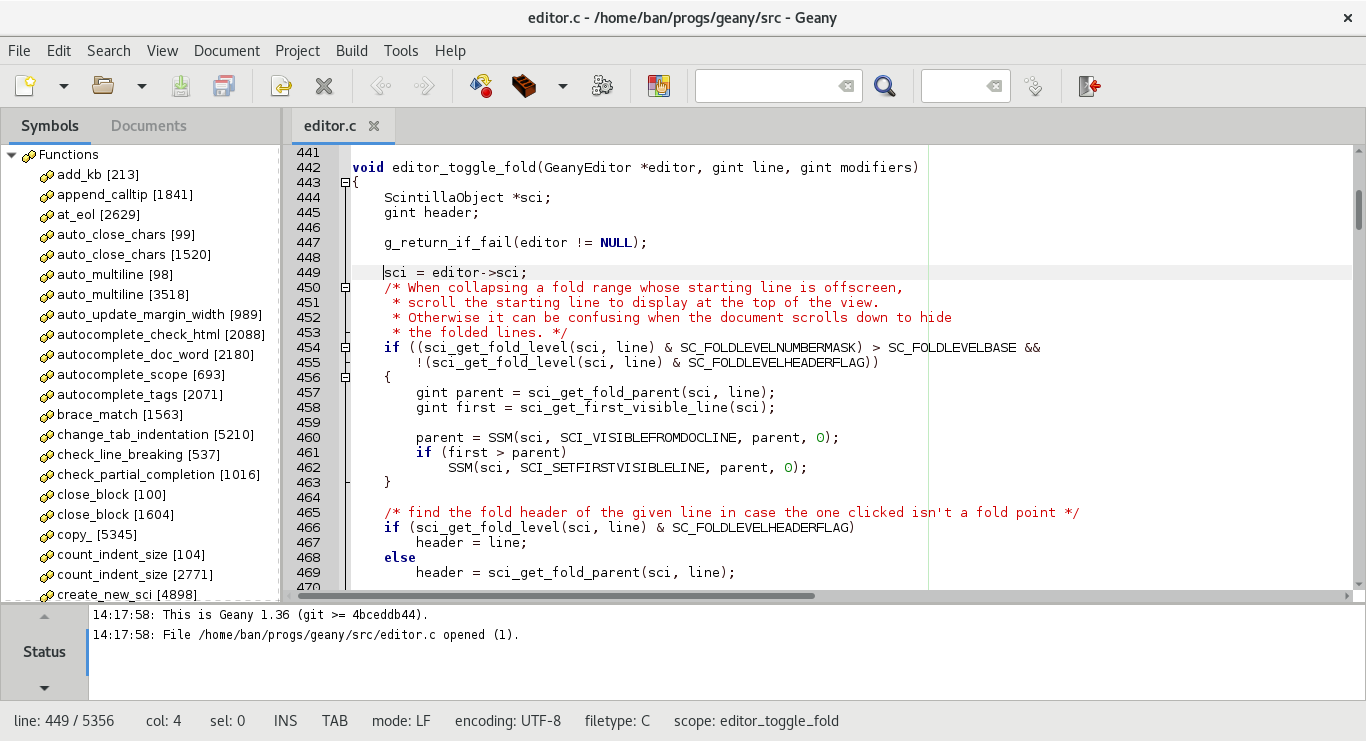 Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash). Geany is a lightweight, fast, and compatible GTK2 based IDE. It supports many languages including but not limited to (PHP, C, C++, Ruby, Python, Bash).
HIEW v7.45
HIEW stands for "Hackers' View". This is an awesome Hex-Editor with many useful functions like assembly code highlighting, detailed info on executables, hex- and assembly editing, string- or code-search, etc. A "must have" for those, who are interested in applications. |
HackBar FireFox addon
 Simple security audit / Penetration test tool. This toolbar will help you in testing sql injections, XSS holes and site security. Simple security audit / Penetration test tool. This toolbar will help you in testing sql injections, XSS holes and site security. |
Hacking For Dummies
 by Kevin Beaver (Author), Stuart McClure (Foreword) "This book is about hacking ethically - the science of testing your computers and network for security vulnerabilities and plugging the holes you find before..." by Kevin Beaver (Author), Stuart McClure (Foreword) "This book is about hacking ethically - the science of testing your computers and network for security vulnerabilities and plugging the holes you find before..." |
Hacking Vs. Security
Hacking Vs. Security is a hacking site, similar to HTS and HBH. It has simulated security challenges, an articles database, forum, etc. |
Hex Workshop
 The Hex Workshop Hex Editor by BreakPoint Software is a complete set of hexadecimal development tools for Microsoft Windows 2000 and later. Hex Workshop combines advanced binary editing and data interpretation with the ease and flexibility of a modern word processor. With the Hex Workshop, you can edit, cut, copy, paste, insert, fill and delete binary data. You can also work with data in its native structure and data types using our integrated structure view and smart bookmarks. Data editing is quick and easy with our extensive features that allow you to: jump to file or sector location, find or replace data, perform arithmetic and logical operations, binary compare files, generate checksums and digests, view character distributions and export data to RTF or HTML for publishing. The Hex Workshop Hex Editor by BreakPoint Software is a complete set of hexadecimal development tools for Microsoft Windows 2000 and later. Hex Workshop combines advanced binary editing and data interpretation with the ease and flexibility of a modern word processor. With the Hex Workshop, you can edit, cut, copy, paste, insert, fill and delete binary data. You can also work with data in its native structure and data types using our integrated structure view and smart bookmarks. Data editing is quick and easy with our extensive features that allow you to: jump to file or sector location, find or replace data, perform arithmetic and logical operations, binary compare files, generate checksums and digests, view character distributions and export data to RTF or HTML for publishing. |
Hydra
THC-Hydra - the best parallized login hacker: for Samba, FTP, POP3, IMAP, Telnet, HTTP Auth, LDAP, NNTP, MySQL, VNC, ICQ, Socks5, PCNFS, Cisco and more. Includes SSL support and is part of Nessus. |
Instructables
 Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com Want to make an explosion or maybe something new for lunch. Instructions on almost anything at instructables.com |
John the Ripper
 John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP/2003 LM hashes, plus several more with contributed patches. John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos AFS and Windows NT/2000/XP/2003 LM hashes, plus several more with contributed patches. |
Kismet
 Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic. Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, decloaking) hidden networks, and infering the presence of nonbeaconing networks via data traffic. Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic. Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, decloaking) hidden networks, and infering the presence of nonbeaconing networks via data traffic. |
LCP
simple to use windows password recovery tool (great for getin into admin acc)free and easy |
Lepton's Crack
Lepton's Crack is a generic password cracker, easily customizable with a simple plug-in system. It can perform a dictionary-based (wordlist) attack, as well as a brute-force (incremental) password scan, including enumeration of a regular expression (useful if you know something about the password) Currently the formats supported are: standard MD4 hash, standard MD5 hash, NT MD4/Unicode, Lotus Domino HTTP password (R4) and SHA-1. Download link is in the directory listing linked at the bottom of the page. |
Linux
 If you want to hack, you need Linux. Windows just won't cut it. If you want to hack, you need Linux. Windows just won't cut it. |
Lost Door v3.2 Stable (Build 2)
 Remote administration tool for Microsoft Windows operating systems. Control and monitor remote computer easily and view what user does. Remote administration tool for Microsoft Windows operating systems. Control and monitor remote computer easily and view what user does. |
MacroMaker
 MacroMaker allows you to create macros or recordings to automate most anything that you already do by hand. MacroMaker was written more for the use of people who regularly use computers and programmers rather than the casual PC user. Most anything you know how to do by hand can be translated into a macro or recording in MacroMaker. If you are having to perform repetitive tasks, this program will help you out tremendiously. The user can simulate a series of keystrokes, mouse events, play back previous recordings of keystrokes and mouse events or execute some built-in functions with just a keystroke. You can even store content from the clipboard in internal MacroMaker buffers for later use. MacroMaker allows you to create macros or recordings to automate most anything that you already do by hand. MacroMaker was written more for the use of people who regularly use computers and programmers rather than the casual PC user. Most anything you know how to do by hand can be translated into a macro or recording in MacroMaker. If you are having to perform repetitive tasks, this program will help you out tremendiously. The user can simulate a series of keystrokes, mouse events, play back previous recordings of keystrokes and mouse events or execute some built-in functions with just a keystroke. You can even store content from the clipboard in internal MacroMaker buffers for later use. |
Md5Decrypter.co.uk Database
Over 13 billion decrypted Md5 hashes. The largest Md5 database online. Crypt and decrypt you hashes. |
Metasploit
 Metasploit is an open-source exploit framework written for unix with mainly windows exploits. Nice tool to write and test your own + exploit into any pc/site with existing payloads. Also comes with online ROR version. Metasploit is an open-source exploit framework written for unix with mainly windows exploits. Nice tool to write and test your own + exploit into any pc/site with existing payloads. Also comes with online ROR version. |
Milw0rm
 A huge archive of exploits, vulnerabilities, shells and flaws. A huge archive of exploits, vulnerabilities, shells and flaws. |
Morpher
 Morphing movie maker for Mac & Windows. Morpher makes digital movies using a 2-D morph between two still images. Morphing movie maker for Mac & Windows. Morpher makes digital movies using a 2-D morph between two still images. |
Net Tools
 Net Tools is a comprehensive set of host monitoring, network scanning, security, administration tools and much more, all with a highly intuitive user interface. It's an ideal tool for those who work in the network security, administration, training, internet forensics or law enforcement internet crimes fields. Net Tools is mainly written in Microsoft Visual Basic 6, Visual C++, Visual C# and Visual Studio .NET. Net Tools is a comprehensive set of host monitoring, network scanning, security, administration tools and much more, all with a highly intuitive user interface. It's an ideal tool for those who work in the network security, administration, training, internet forensics or law enforcement internet crimes fields. Net Tools is mainly written in Microsoft Visual Basic 6, Visual C++, Visual C# and Visual Studio .NET. |
Netcat
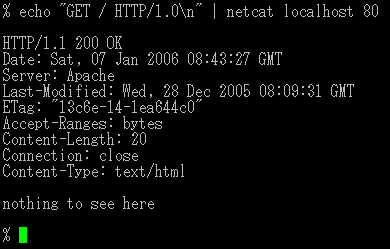 Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder. Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. It is designed to be a reliable "back-end" tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It provides access to the following main features: * Outbound and inbound connections, TCP or UDP, to or from any ports. * Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel. * Built-in port-scanning capabilities, with randomizer. * Advanced usage options, such as buffered send-mode (one line every N seconds), and hexdump (to stderr or to a specified file) of trasmitted and received data. * Optional RFC854 telnet codes parser and responder. |
Nikto
 Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 3300 potentially dangerous files/CGIs, versions on over 625 servers, and version specific problems on over 230 servers. Scan items and plugins are frequently updated and can be automatically updated (if desired). Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 3300 potentially dangerous files/CGIs, versions on over 625 servers, and version specific problems on over 230 servers. Scan items and plugins are frequently updated and can be automatically updated (if desired). |
Nmap
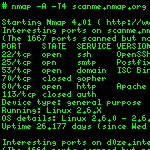 Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. |
Nmap Online
A web based implement of the popular port scanning utility, Nmap. |
Nmap/NmapFE(GUI)
 Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and both console and graphical versions are available. |
NoScript
 The NoScript Firefox extension provides extra protection for Firefox, Flock, Seamonkey and others mozilla-based browsers: this free, open source add-on allows JavaScript and Java execution only for trusted domains of your choice (e.g. your home-banking web site). NoScript optionally blocks Flash and other potentially exploitable plugins too, and provides the most powerful Anti-XSS protection available in a browser. <img src="http://software.informaction.com/data/wc06.jpg"> The NoScript Firefox extension provides extra protection for Firefox, Flock, Seamonkey and others mozilla-based browsers: this free, open source add-on allows JavaScript and Java execution only for trusted domains of your choice (e.g. your home-banking web site). NoScript optionally blocks Flash and other potentially exploitable plugins too, and provides the most powerful Anti-XSS protection available in a browser. <img src="http://software.informaction.com/data/wc06.jpg"> |
Notepad ++
 Notepad++ is a free source code editor (and Notepad replacement), which supports several programming languages, running under the MS Windows environment. Notepad++ is a free source code editor (and Notepad replacement), which supports several programming languages, running under the MS Windows environment. |
OWASP Web application Testing guide
 The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. The OWASP Testing Guide includes a "best practice" penetration testing framework which users can implement in their own organizations and a "low level" penetration testing guide that describes techniques for testing most common web application and web service security issues. |
Okteta
 Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well! Okteta is a simple editor for the raw data of files. This type of program is also called hex editor or binary editor. Now that KDE is cross platform, this program can not only be used on Linux, but on Windows and MacOSx as well! |
Oldschoolphreak
Good information on phone hacking and other methods. |
PHP.net
 PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section. PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. If you are new to PHP and want to get some idea of how it works, try the introductory tutorial. After that, check out the online manual, and the example archive sites and some of the other resources available in the links section. |
Peer Guardian
Peer Guardian is Phoenix Labs’ premier IP blocker. Peer Guardian integrates support for multiple lists, list editing, automatic updates, and blocking all of IPv4 (TCP, UDP, ICMP, etc), making it the safest and easiest way to protect your privacy on P2P. It currently has a Windows, Linux, Lite, and OSX version. It blocks Government, Anti-P2P, Education, Virus, Spyware, and other I.P.s. This is a highly recommended tool. It also supports your own custom block list of I.P.s. |
Phreaks and Geeks
Good information on Phreaking and phone hacking. |
Physics Illustrator
A motion simulator for the Tablet PC that demonstrates physics by using objects that are drawn by the user. |
Process Explorer
.jpg) Ever wondered which program has a particular file or directory open? Now you can find out. Process Explorer shows you information about which handles and DLLs processes have opened or loaded. The Process Explorer display consists of two sub-windows. The top window always shows a list of the currently active processes, including the names of their owning accounts, whereas the information displayed in the bottom window depends on the mode that Process Explorer is in: if it is in handle mode you'll see the handles that the process selected in the top window has opened; if Process Explorer is in DLL mode you'll see the DLLs and memory-mapped files that the process has loaded. Process Explorer also has a powerful search capability that will quickly show you which processes have particular handles opened or DLLs loaded. Ever wondered which program has a particular file or directory open? Now you can find out. Process Explorer shows you information about which handles and DLLs processes have opened or loaded. The Process Explorer display consists of two sub-windows. The top window always shows a list of the currently active processes, including the names of their owning accounts, whereas the information displayed in the bottom window depends on the mode that Process Explorer is in: if it is in handle mode you'll see the handles that the process selected in the top window has opened; if Process Explorer is in DLL mode you'll see the DLLs and memory-mapped files that the process has loaded. Process Explorer also has a powerful search capability that will quickly show you which processes have particular handles opened or DLLs loaded. |
Process Hacker
 Process Hacker is a tool for viewing and manipulating processes and their threads, modules, memory and handles, and viewing and editing services. It can also read/write process memory and search through process memory using literal bytes or regular expressions. It can view the command line and current directory of a process, view/edit its DEP status, and even DRM-protect and unprotect it. It can run programs as another user or as SYSTEM, LOCAL SERVICE or NETWORK SERVICE if you have administator privileges. This is achieved using a helper program which is installed as a system service (similar to PsExec). It loads symbols from various libraries automatically and uses them when displaying the call stacks of threads (just like Process Explorer). It also has a disassembler derived from OllyDbg's which can be accessed when viewing PE files' exports. It can bypass most kernel-mode hooks and user-mode hooks on ZwOpenProcess, ZwOpenThread and ZwOpenProcessToken. Process Hacker is a tool for viewing and manipulating processes and their threads, modules, memory and handles, and viewing and editing services. It can also read/write process memory and search through process memory using literal bytes or regular expressions. It can view the command line and current directory of a process, view/edit its DEP status, and even DRM-protect and unprotect it. It can run programs as another user or as SYSTEM, LOCAL SERVICE or NETWORK SERVICE if you have administator privileges. This is achieved using a helper program which is installed as a system service (similar to PsExec). It loads symbols from various libraries automatically and uses them when displaying the call stacks of threads (just like Process Explorer). It also has a disassembler derived from OllyDbg's which can be accessed when viewing PE files' exports. It can bypass most kernel-mode hooks and user-mode hooks on ZwOpenProcess, ZwOpenThread and ZwOpenProcessToken. |
Protable Apps
Portable Applications that you can take anywhere on your flash drive such as: browsers, anti virus, games, utilities and much more. |
PuTTY
 PuTTY is a client program for the SSH, Telnet and Rlogin network protocols. These protocols are all used to run a remote session on a computer, over a network. PuTTY implements the client end of that session: the end at which the session is displayed, rather than the end at which it runs. In really simple terms: you run PuTTY on a Windows machine, and tell it to connect to (for example) a Unix machine. PuTTY opens a window. Then, anything you type into that window is sent straight to the Unix machine, and everything the Unix machine sends back is displayed in the window. So you can work on the Unix machine as if you were sitting at its console, while actually sitting somewhere else. PuTTY is a client program for the SSH, Telnet and Rlogin network protocols. These protocols are all used to run a remote session on a computer, over a network. PuTTY implements the client end of that session: the end at which the session is displayed, rather than the end at which it runs. In really simple terms: you run PuTTY on a Windows machine, and tell it to connect to (for example) a Unix machine. PuTTY opens a window. Then, anything you type into that window is sent straight to the Unix machine, and everything the Unix machine sends back is displayed in the window. So you can work on the Unix machine as if you were sitting at its console, while actually sitting somewhere else. |
Python
 Python is a dynamic object-oriented programming language that can be used for many kinds of software development. It offers strong support for integration with other languages and tools, comes with extensive standard libraries, and can be learned in a few days. Many Python programmers report substantial productivity gains and feel the language encourages the development of higher quality, more maintainable code. Python is a dynamic object-oriented programming language that can be used for many kinds of software development. It offers strong support for integration with other languages and tools, comes with extensive standard libraries, and can be learned in a few days. Many Python programmers report substantial productivity gains and feel the language encourages the development of higher quality, more maintainable code. |
RefControl
A Firefox addon to control what gets sent as the HTTP Referer on a per-site basis. |
Remote Exploit's Backtrack 3
 This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out! This is a VERY useful Linux Slax live CD developed for Penetration Testing. All you need to do is burn the .iso image to a CD and boot to it after a restart on any computer. BT3 has a NICE collection of tools that can be used for hacking, windows password cracking,network mapping, and a bunch of other fun tools to mess around with. It also has KDE and Flux, so it has a very friendly GUI. Check it out! |
ResizeEnable
 ResizeEnable lets you turn usually non-resizeable windows into resizeable windows. ResizeEnable lets you turn usually non-resizeable windows into resizeable windows. |
Ruby
 A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write. A dynamic, open source programming language with a focus on simplicity and productivity. It has an elegant syntax that is natural to read and easy to write. |
S-Tools
S-Tools is a stenography tool that hides files in BMP, GIF, and WAV files. You open up a copy of S-Tools and drag pictures and sounds across to it. To hide files you just drag them over open sound/picture windows. You can hide multiple files in one sound/picture and your data is compressed before being encrypted then hidden. Multi-threaded operation means that you can have many hide/reveal operations going simultaneously without fear of them interfering with you or holding up your work. You can even close the original picture/sound with no ill effects to ongoing threads. Encryption services come courtesy of "cryptlib" by Peter Gutmann (and others). |
SUPERAntiSpyware
 Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits. Finds and removes spyware, adware, malware, keyloggers, trojans, and rootkits. |
Sam Spade
 General-purpose Internet utility - ping - nslookup - whois - IP block - dig - traceroute finger - SMTP VRFY - web browser keep-alive - DNS zone transfer - SMTP relay check - Usenet cancel check - website download - website search - email header analysis - Email blacklist - query Abuse address General-purpose Internet utility - ping - nslookup - whois - IP block - dig - traceroute finger - SMTP VRFY - web browser keep-alive - DNS zone transfer - SMTP relay check - Usenet cancel check - website download - website search - email header analysis - Email blacklist - query Abuse address |
Sandboxie
 Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data in your computer. Sandboxie runs your programs in an isolated space which prevents them from making permanent changes to other programs and data in your computer. |
Snort
 SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry. SNORT® is an open source network intrusion prevention and detection system utilizing a rule-driven language, which combines the benefits of signature, protocol and anomaly based inspection methods. With millions of downloads to date, Snort is the most widely deployed intrusion detection and prevention technology worldwide and has become the de facto standard for the industry. |
SnortSam
 SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls. SnortSam is a plugin for Snort, an open-source light-weight Intrusion Detection System (IDS). The plugin allows for automated blocking of IP addresses on several firewalls. |
Spybot - Search & Destroy
 The best spyware protection software you can ever find. The best spyware protection software you can ever find. |
Sysinternals Suite
.gif) The Sysinternals Troubleshooting Utilities have been rolled up into a single Suite of tools. This file contains the individual troubleshooting tools and help files. It does not contain non-troubleshooting tools like the BSOD Screen Saver or NotMyFault. The Sysinternals Troubleshooting Utilities have been rolled up into a single Suite of tools. This file contains the individual troubleshooting tools and help files. It does not contain non-troubleshooting tools like the BSOD Screen Saver or NotMyFault. |
T E X T F I L E S
 Lots on info and articles that's been compiled over the years...many topics...worth reading Lots on info and articles that's been compiled over the years...many topics...worth reading |
T-Search
T-Search is a program that lets you search for values that are stored or downloaded into memory. This program, is usually used to hack games! |
TOR
 Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, IRC, SSH, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features. Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, IRC, SSH, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features. |
Turbo
 Turbo is a software "Turbo Switch". You may set the effective CPU speed anywhere from 1 to 100% of full speed. All programs will execute at the reduced CPU speed set by Turbo. Works with Win/9x and Win/NT. Freeware. Turbo is a software "Turbo Switch". You may set the effective CPU speed anywhere from 1 to 100% of full speed. All programs will execute at the reduced CPU speed set by Turbo. Works with Win/9x and Win/NT. Freeware. |
Tuts 4 You
 This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more. This site is dedicated to all the researchers and reverse engineers interested in Reverse Code Engineering (RCE) techniques and practices and all things related. You will be able to find a wide breadth of information retained on this site to help in your research ranging from; anti-debugging, virtual machines, unpacking, coding, disassembling, debugging, keygenning, cryptography and much, much more. |
Visual IRC
It is a FREE IRC client that is very good and so far error free. PLus has various ways to customize things. |
W3Schools
 At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages. At W3Schools you will find all the Web-building tutorials you need, from basic HTML and XHTML to advanced XML, SQL, Database, Multimedia and WAP, Totally Free. Great for people new to computer languages. |
Web Developer [Toolbar]
Firefox add-on. This toolbar allows you to edit and view parts of a webpage in a user-friendly way, even when they are not normally so obvious. (Great for HTS) |
Webgoat
 WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson. |
Win SCP
sftp client |
WinDirStat
 WinDirStat (WDS) is a disk usage statistics viewer and cleanup tool for Windows. It shows disk, file and directory sizes in a treelist as well as graphically in a treemap, much like KDirStat or SequoiaView. WinDirStat (WDS) is a disk usage statistics viewer and cleanup tool for Windows. It shows disk, file and directory sizes in a treelist as well as graphically in a treemap, much like KDirStat or SequoiaView. |
WinSock Packet Editor
WinSock Packet Editor (WPE) Is A Packet Sniffer / Injector For Windows. A Useful Packet Editing Tool. |
Wireshark
 Network protocol analyzer for Windows and Unix that allows examination of data from a live network, or from a capture file on disk. Network protocol analyzer for Windows and Unix that allows examination of data from a live network, or from a capture file on disk. |
XVI32
 XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP. XVI32 is a freeware hex editor running under Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP. |
distrowatch
Yeah, Find the distro you want  |
dsniff
dsniff is a collection of tools for network auditing and penetration testing. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.). arpspoof, dnsspoof, and macof facilitate the interception of network traffic normally unavailable to an attacker (e.g, due to layer-2 switching). sshmitm and webmitm implement active monkey-in-the-middle attacks against redirected SSH and HTTPS sessions by exploiting weak bindings in ad-hoc PKI. |
freeBSD
 meh if you don't know what that is... FreeBSD® is an advanced operating system for x86 compatible (including Pentium® and Athlon™), amd64 compatible (including Opteron™, Athlon™64, and EM64T), UltraSPARC®, IA-64, PC-98 and ARM architectures. It is derived from BSD, the version of UNIX® developed at the University of California, Berkeley. It is developed and maintained by a large team of individuals. Additional platforms are in various stages of development. meh if you don't know what that is... FreeBSD® is an advanced operating system for x86 compatible (including Pentium® and Athlon™), amd64 compatible (including Opteron™, Athlon™64, and EM64T), UltraSPARC®, IA-64, PC-98 and ARM architectures. It is derived from BSD, the version of UNIX® developed at the University of California, Berkeley. It is developed and maintained by a large team of individuals. Additional platforms are in various stages of development. |
hexcat
Hexcat (hexcat) is a UNIX/Linux hex editor that outputs the source in hexadecimal/plaintext/bin in three seperate columns. This output can be streamed like the other UNIX commands, such as 'cat'. (The link is for Debian-based systems) |
iMacro
Firefox add-on. Records what you do then repeats as many times as you want |
ophcrack
Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms. Features: * » Runs on Windows, Linux/Unix, Mac OS X, ... * » Cracks LM and NTLM hashes. * » Free tables available for Windows XP and Vista. * » Brute-force module for simple passwords. * » LiveCD available to simplify the cracking. * » Loads hashes from encrypted SAM recovered from a Windows partition, Vista included. * » Free and open source software (GPL). |
pic2ascii
 pic2ascii is a freeware tool to transform bitmaps (pictures) to ascii information (text). pic2ascii is a freeware tool to transform bitmaps (pictures) to ascii information (text). |
socat
socat is a relay for bidirectional data transfer between two independent data channels. Each of these data channels may be a file, pipe, device (serial line etc. or a pseudo terminal), a socket (UNIX, IP4, IP6 - raw, UDP, TCP), an SSL socket, proxy CONNECT connection, a file descriptor (stdin etc.), the GNU line editor (readline), a program, or a combination of two of these. These modes include generation of "listening" sockets, named pipes, and pseudo terminals. tl;dr a better netcat with more capability |
tlbox (tool box)
 This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux. This site offers a collection of tutorials, articles, and programs useful for people interested in programing, system administration, and web design for Windows, Mac, or Linux. |
webDOMinator
 The webDOMinator is a bot that allows for automation of all actions online through super-scripting. Build up online profiles, start massive PM campaigns, automatic user lists, commenting, and utilizes super-scripts to get around most security on a web site The webDOMinator is a bot that allows for automation of all actions online through super-scripting. Build up online profiles, start massive PM campaigns, automatic user lists, commenting, and utilizes super-scripts to get around most security on a web site |
|
|
|
|
|
|
|
|
|
|
|
|
 |
|
Sponsored |
|
|
|
|
Today, there have been 10 visitors (14 hits) on this page! |